Headline News: New Legislation, 3.15 Evening, a New Page in Network Security History Turned Over in Spring Breeze
2017-03-17
In this year’s NPC and CPPCC, the Individual information protection was formally written into the General Provisions of Civil Law of the People’s Republic of China. In the 3.15 Evening (or, March 15 Evening) broadcasted two days ago, the network information security once again become the focus of media attention. Telecommunication fraud, security holes in AI identification systems, and other network information security problems were called to face the music. The worries about the negative social influence of those network information security problems are rising in Chinese IT industry.

The fast changing in social consumption structure and people’s ideas and ways of consumption has already made the information security in new consumption areas a problem that everyone has to deal with seriously. In this era of Internet of Everything, one small information security breach could lead to a huge storm causing numerous social and economic losses.
Before the 3.15 Evening, there had already emerged quite a number of reports about people suffering from network information security problems. Incidents like Hillary Clinton’s Email Controversy, a great sensation in the world, and the “Eavesdropping Dolls”, had already set off alarm bells in people’s mind about their network information security. Now, let’s have a brief review about these incidents.


Hillary Clinton’s Email Controversy revealed the security vulnerabilities in private Email servers?
During the US Presidential Election, a Romanian hacker exposed the existence of Hillary Clinton’s private Email servers, which soon developed into a political storm.


DDoS attacks, another challenge to IoT security?
In 2016, a hacker launched a DDoS attack via Mirai (a Botnet) onto the servers of a US domain name server (DNS) company, the Dyn, which eventually left over a half of American people disconnected from their internet services.


With a security breach in an APP terminal, could everyone turn a doll into an eavesdropper?
“Cayla” is a toy doll supporting wireless connection with a smart phone or a computer via an APP. But, when a hacker takes over its control, it could serve as an eavesdropping device in people’s families. In fear of that situation, the German Federal Network Agency banned the selling of this type of toy dolls.

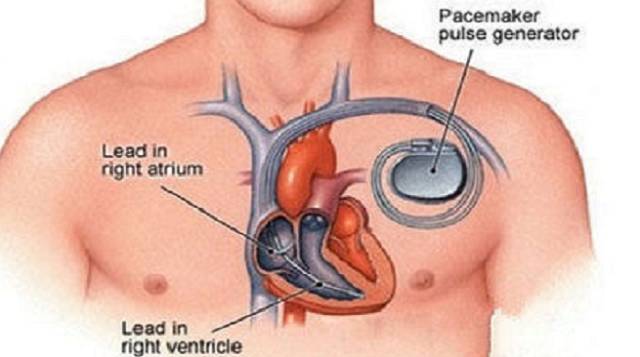
黑客攻击,救命的“稻草”也能变“杀人武器“?Under a hacker attack, could a life-saving device be turned into a killing weapon?
According to a recent study, the cardiac pacemaker is under the threat of hacker attacks. A hacker could either steal the personal information of a patient, or speed up the power consumption of the battery pack, or inject malicious information into a pacemaker’s processor. No matter what it may be, it will lead to terrible consequences.
All these cases point to one fact: the network information security environment is getting increasingly complicated, or, to put it in another way, people’s information security is under greater risk or threat than ever. The network security has become a great concern of all people around the world. The world governments have began considering the network information security at the level of national strategic security. On the other hand, as Cloud computing is getting wider recognition and greater acceptance in the market, more and more application scenarios have begun emerging, which makes the information security technologies all the more important. In short, the higher the requirements of the society on security, availability and effectiveness of IT services go, the greater the challenge on the capacity of the industry in network information security will be.


By improving the security level of the internal code of its APP, an internet finance platform largely improved its protection over its users’ trading activities and private information;
2、Network Security: Internet of Vehicles
By deploying a security protection system, a large automaker effectively improved the defense capability of its vehicle terminals and its network management equipments and, subsequently, ensured the reliability and stability of the remote controlling system of vehicle APP products.
3、Network Security: Smart Home
A smart home equipment manufacturer found out that there were a few security holes in the APP or control terminals of its products that might fall victim to hacker attacks. Then, by deploying and implementing information security solutions, the security hazards were eliminated.
4、Network Security: Airport
After deploying an information security solution, an airport has gotten the network-wide intelligence detection capability and is able to quickly respond to security threats and work out tailored defense strategies against hacker attacks in real time.
Although, in many organizations, the consciousness of network information security is awakening, there is still a long way to go to really solve the network information security problems. As an industry-leading datacenter service provider in China, SDS is committed to meeting network information security needs of enterprises operating in different industries with professional and reliable products, services and strong supports.
In addition to all the requirements on the installation and use of above-mentioned software, the SDS Cloud Desktop can largely improve the data security level of virtual machines. For example, it can meet access control needs and a series of other security needs. Secondly, it can meet a variety of management needs, including remote problem solving, O&M management, restructuring, system refreshing, and balancing, and all other things that could improve management efficiency and effectiveness. Finally, it supports the connection and use of special external equipments widely used in the industry. In fact, the feature of SDS Cloud Desktop may be summarized in one line ‘Leader of enterprise information security service meeting high security needs’.
Considering the close relation between the network and our work and life, it’s foreseeable that the network information security will get more important. And it requires the participation and cooperation of all parties to realize network information security and build a green network ecosystem.
SDS is committed to meeting network information security needs of enterprises operating in different industries with professional and reliable products, services and strong supports.
 中文
中文




